本帖最后由 liudejun 于 2023-12-22 23:18 编辑
对PDF Printer for Windows 7的逆向爆破方法教程这几个就是Delphi写的外壳程序而已 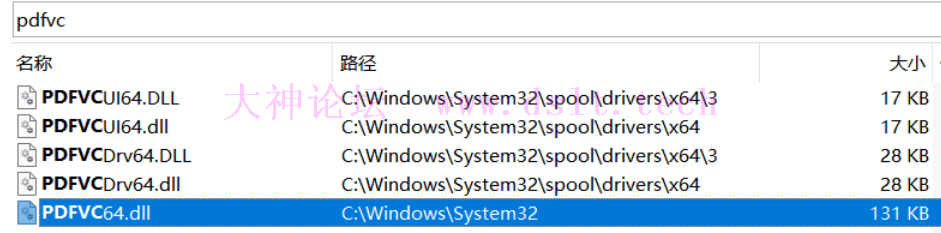
再用Everything搜一下,x64dbg打开依次看一眼。
立马得出结论 ,最后一个DLL里边有猫腻 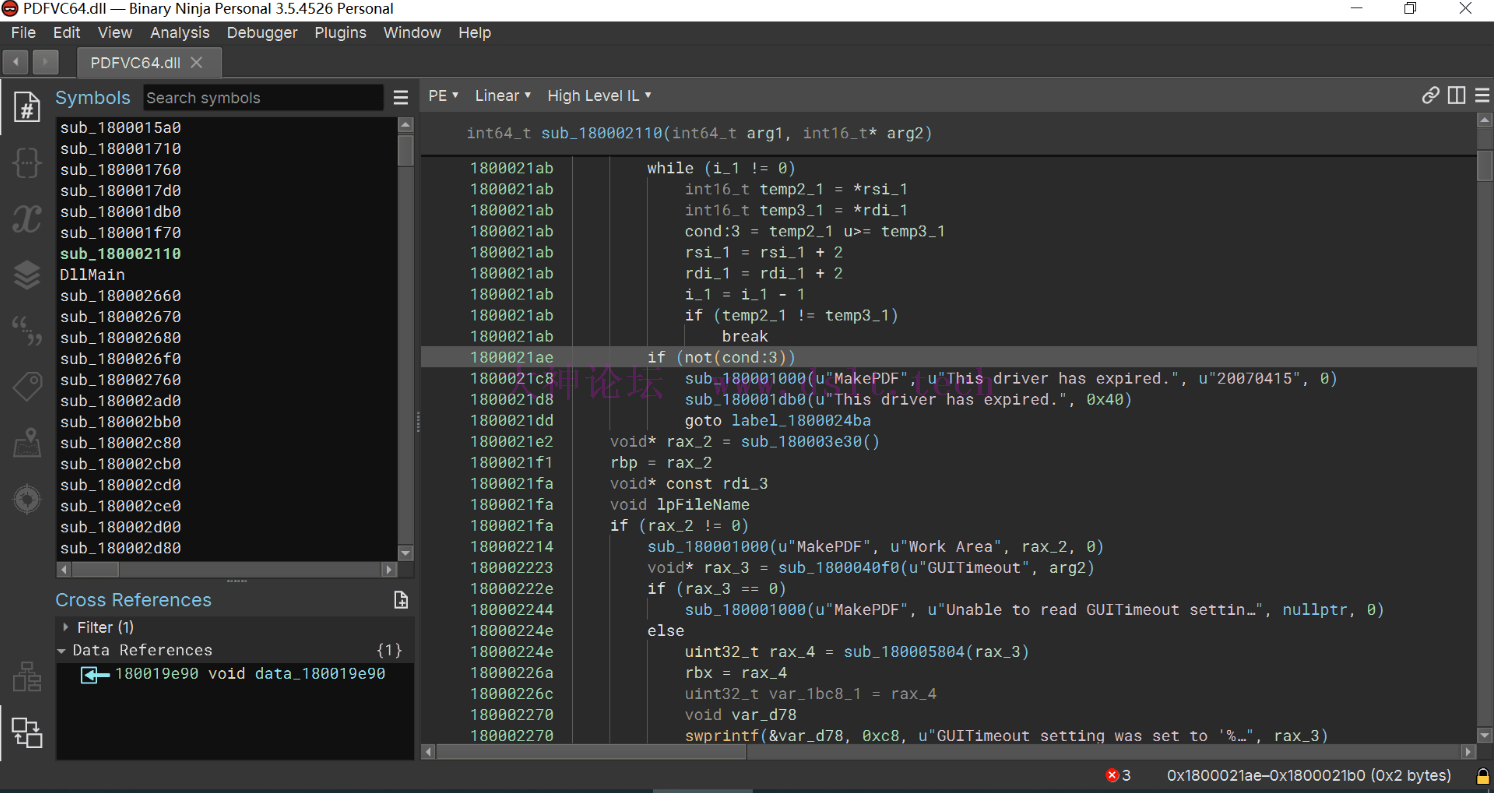
真正的核心代码在这里!
180002129 __chkstk(0x1bd0)
180002138 void var_1be8
180002138 int64_t rax_1 = data_18001f0f0 ^ &var_1be8
180002143 bool cond:1 = true
180002143 bool cond:3 = true
180002146 void* const rsi = u"PDFPort"
18000214d void* const rdi = u"PDFPort"
180002154 int64_t i = 8
18000215c void* rbp = nullptr
18000215f while (i != 0)
18000215f int16_t temp0_1 = *rsi
18000215f int16_t temp1_1 = *rdi
18000215f cond:1 = temp0_1 == temp1_1
18000215f cond:3 = temp0_1 u>= temp1_1
18000215f rsi = rsi + 2
18000215f rdi = rdi + 2
18000215f i = i - 1
18000215f if (temp0_1 != temp1_1)
18000215f break
180002162 uint32_t rbx = 0
180002165 if (not(cond:1))
18000216c void var_1bb8
18000216c sub_1800055ec(&var_1bb8)
18000217b void var_1bb0
18000217b sub_1800052bc(&var_1bb0, &var_1bb8)
180002195 void var_1b88
180002195 _mbccpy_s(&var_1b88, 0x1e, u"%Y%m%d", &var_1bb0)
18000219a void* const rsi_1 = u"20070415"
1800021a1 void* rdi_1 = &var_1b88
1800021a6 int64_t i_1 = 9
1800021ab while (i_1 != 0)
1800021ab int16_t temp2_1 = *rsi_1
1800021ab int16_t temp3_1 = *rdi_1
1800021ab cond:3 = temp2_1 u>= temp3_1
1800021ab rsi_1 = rsi_1 + 2
1800021ab rdi_1 = rdi_1 + 2
1800021ab i_1 = i_1 - 1
1800021ab if (temp2_1 != temp3_1)
1800021ab break
1800021ae if (not(cond:3))
1800021c8 sub_180001000(u"MakePDF", u"This driver has expired.", u"20070415", 0)
1800021d8 sub_180001db0(u"This driver has expired.", 0x40)
1800021dd goto label_1800024ba
1800021e2 void* rax_2 = sub_180003e30()
1800021f1 rbp = rax_2
1800021fa void* const rdi_3
1800021fa void lpFileName
1800021fa if (rax_2 != 0)
180002214 sub_180001000(u"MakePDF", u"Work Area", rax_2, 0)
180002223 void* rax_3 = sub_1800040f0(u"GUITimeout", arg2)
18000222e if (rax_3 == 0)
180002244 sub_180001000(u"MakePDF", u"Unable to read GUITimeout settin…", nullptr, 0)
18000224e else
18000224e uint32_t rax_4 = sub_180005804(rax_3)
18000226a rbx = rax_4
18000226c uint32_t var_1bc8_1 = rax_4
180002270 void var_d78
180002270 swprintf(&var_d78, 0xc8, u"GUITimeout setting was set to '%…", rax_3)
180002278 j_free(rax_3)
180002282 if (rbx s< 0)
180002282 rbx = -1
180002299 sub_180004050(&lpFileName, 0x104, &data_180021c70)
1800022b7 sub_180001000(u"MakePDF", u"PostScript", &lpFileName, 0)
1800022d0 sub_180001000(u"MakePDF", u"Build parameter string for GUI", nullptr, 0)
1800022ee sub_180001000(u"MakePDF", u"Postscript file", &lpFileName, 0)
180002307 void var_1938
180002307 sub_180004f24(&var_1938, 0x5dc, u"ps="")
180002321 sub_180004d7c(&var_1938, 0x5dc, &lpFileName)
18000233a sub_180004d7c(&var_1938, 0x5dc, &data_180019b4c)
180002353 sub_180004d7c(&var_1938, 0x5dc, u", sessionid="")
18000236c sub_180004d7c(&var_1938, 0x5dc, &data_180021c70)
180002385 sub_180004d7c(&var_1938, 0x5dc, &data_180019b4c)
1800023a2 sub_180001000(u"MakePDF", u"Document Name is ", &data_1800208e0, 0)
1800023bb sub_180004d7c(&var_1938, 0x5dc, u", doc="")
1800023ea void var_be8
1800023ea sub_180004d7c(&var_1938, 0x5dc, sub_180001760(&data_1800208e0, &var_be8, 0x5dc))
180002403 sub_180004d7c(&var_1938, 0x5dc, &data_180019b4c)
18000240b if (arg2 != 0)
180002421 sub_180001000(u"MakePDF", u"Printer Name is ", arg2, 0)
18000243a sub_180004d7c(&var_1938, 0x5dc, u", printer="")
180002465 sub_180004d7c(&var_1938, 0x5dc, sub_180001760(arg2, &var_be8, 0x5dc))
18000247e sub_180004d7c(&var_1938, 0x5dc, &data_180019b4c)
18000249c sub_180001000(u"MakePDF", u"GUI parameters", &var_1938, 0)
1800024b5 if (sub_180001f70(&var_1938, rbx, arg2) == 0)
1800024b5 goto label_1800024ba
180002509 rdi_3 = u"Success"
180002203 else
180002203 sub_180001000(u"MakePDF", u"Unable to determine Work Area", rax_2, 0)
1800024ba label_1800024ba:
1800024ba rdi_3 = u"Error"
1800024c8 if (sub_180001430(arg2) == 0 && sub_180001530(&lpFileName) != 0)
1800024f4 sub_180001000(u"MakePDF", u"Remove PS file", &lpFileName, 0)
180002501 DeleteFileW(&lpFileName)
18000252a sub_180001000(u"MakePDF", u"Cleanup", nullptr, 0)
180002532 free(rbp)
18000254b sub_180001000(u"MakePDF", u"Status", rdi_3, 0)
18000257f return __security_check_cookie(rax_1 ^ &var_1be8)
这段代码的大致意思就是。。。生成pdf(写入过程),一旦驱动过期。。
打印的时候 根据 Postscript file 输出红色水印。 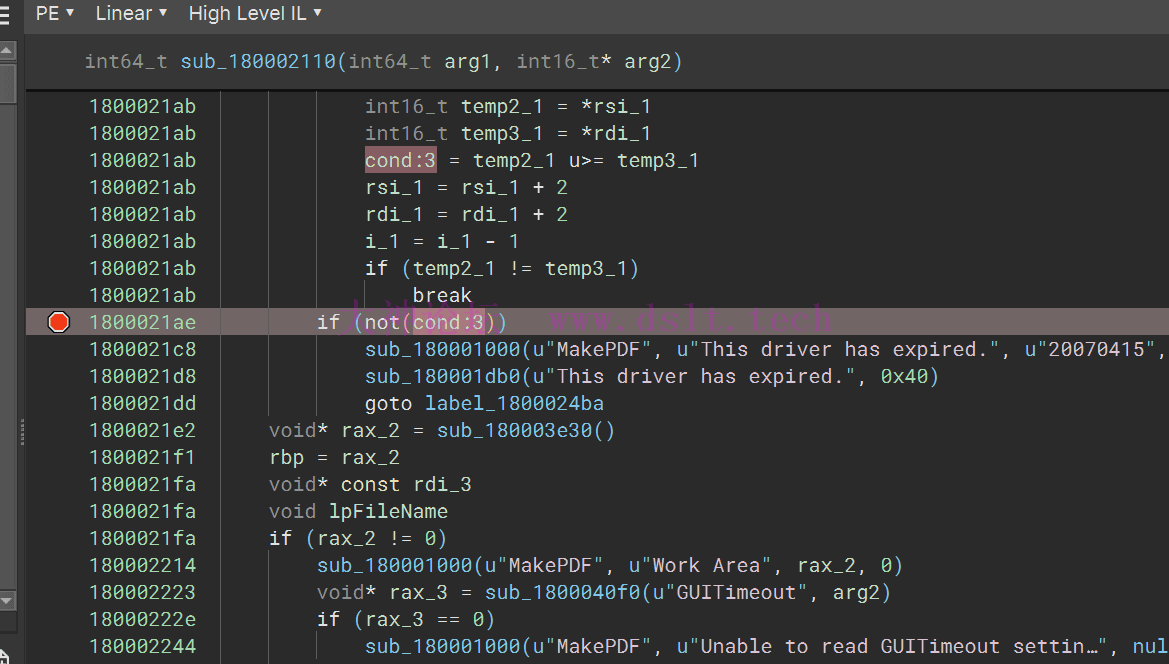
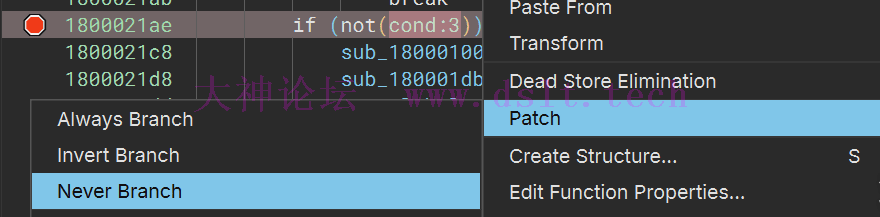
所以根据伪代码的逻辑,来修改代码逻辑,补丁过后别忘记保存 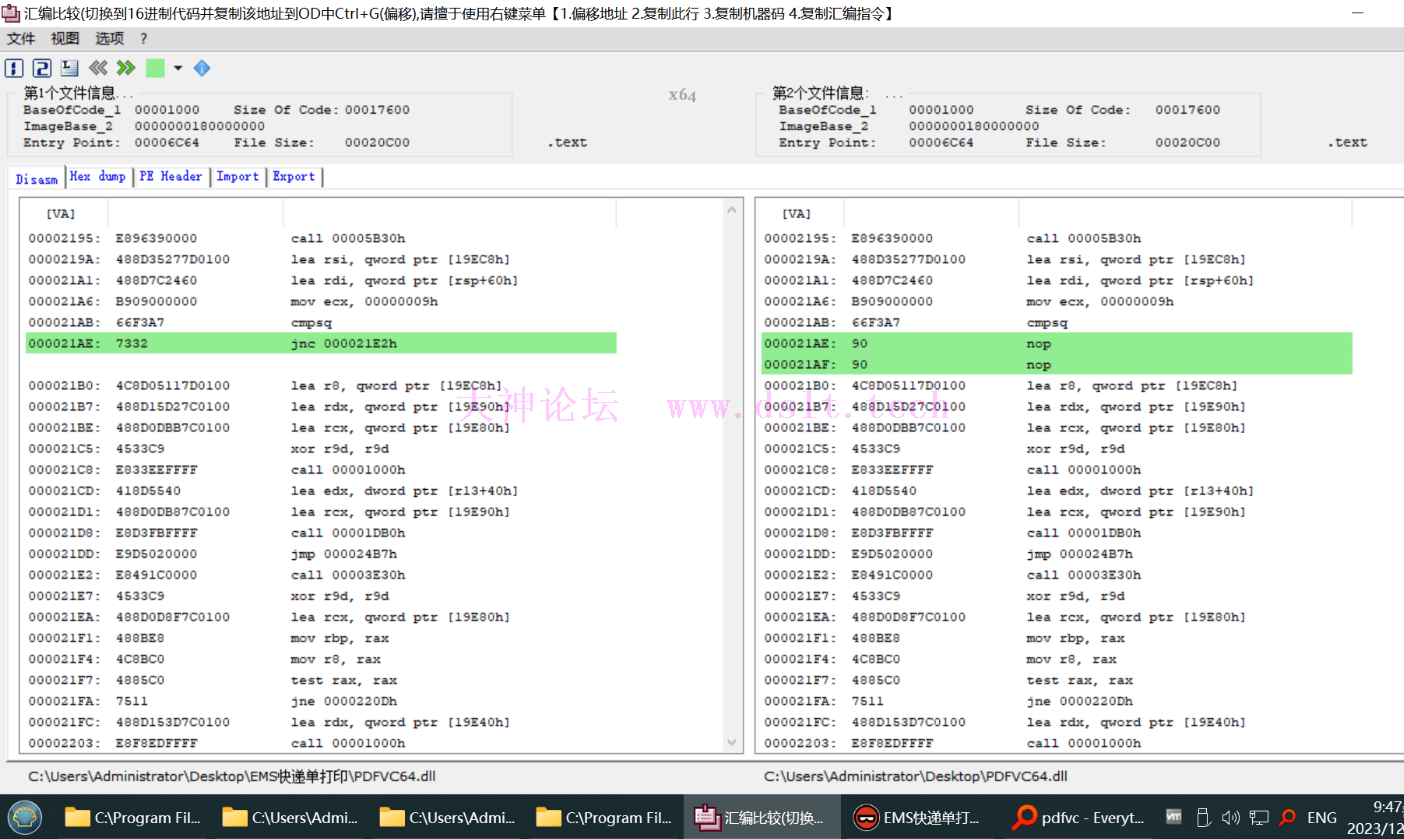
最终再来欣赏下修改的效果。 PS最后的Patch配图选错了,该是反转或总是成立(操作太快,手滑了),懒的改凑合看吧。 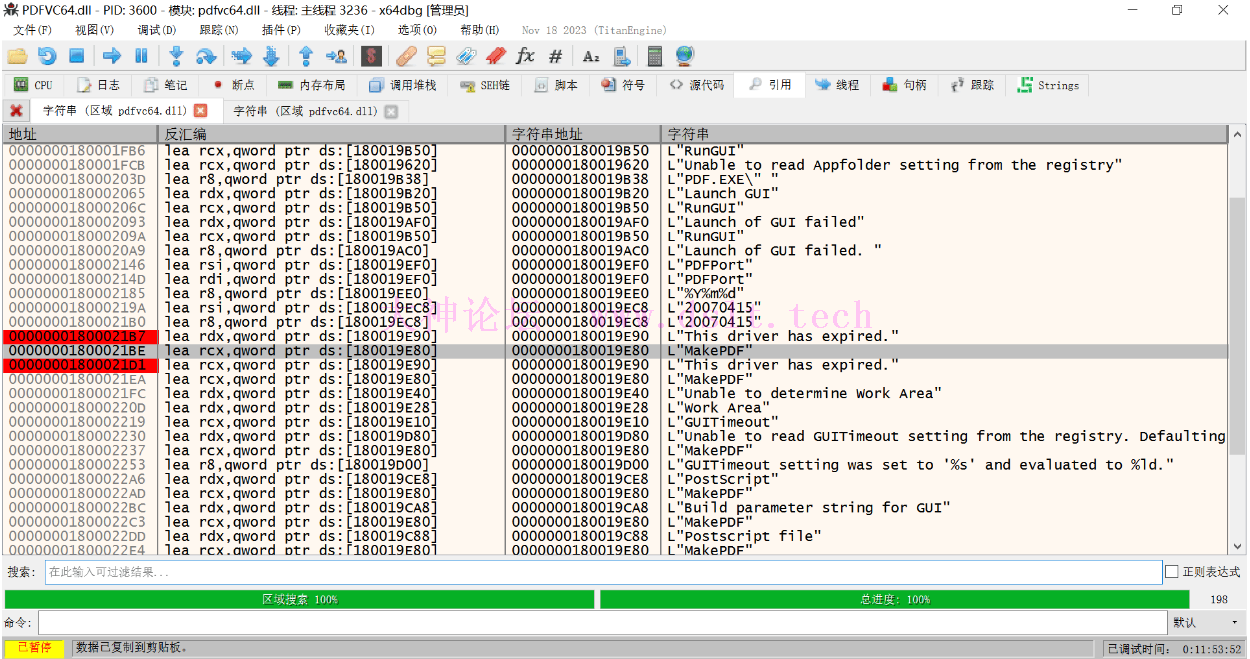
注:若转载请注明大神论坛来源(本贴地址)与作者信息。
|

 发表于 2023-12-22 23:18
发表于 2023-12-22 23:18